NSS初窥
版本 0.01
在使用wireshark分析https时,加密传输的内容会解析失败。而NSS可以存储TLS握手过程中的Key,用于解密。很好奇,它是如何实现的?
wireshark配置
Edit→Preferences→Protocols→SSL→(Pre)-Master-Secret log filename.
key log文件格式
文件的格式:<Label> <space> <ClientRandom> <space> <Secret>
比较常见的Label和对应日志的内容:
CLIENT_HANDSHAKE_TRAFFIC_SECRET
CLIENT_RANDOM
CLIENT_TRAFFIC_SECRET_0
EXPORTER_SECRET
SERVER_HANDSHAKE_TRAFFIC_SECRET
SERVER_TRAFFIC_SECRET_0
CLIENT_RANDOM 8e40057e8e1c32f42faf87ddc17a81da9e02aa6c4ef4fcec2dcb504982e50691 0df84b6a904cb47940666a9e198dceab94b58dd0f0e61775db52716a37759d25b600b44601b541f5b21669ef0814770e
CLIENT_HANDSHAKE_TRAFFIC_SECRET 9aef967472d9d65bf269989ac68c68c6374fd8c2cf9edf98c91593c8df7ffa3f 23b0b29e3edfe6e53114c6d9cb85159902462801c5540fc806c09f5d1711d992
CLIENT_TRAFFIC_SECRET_0 cd12af49c901682f29777821369c167854b047ac27a6a85c3db9dce565debbcf f826d8181c8b751cafd8c60bdbe2e4a4974113eea2a46c2a615e2115d70c9544
EXPORTER_SECRET 51c27befc24dceb18ade59b4a10c1398725848f7130b2ebeeb2e01483ed95e4d 58cc23d6d1db1e674200f7457dc9833ec826a5faf71830a6c5d3f4e63fa2144f
TLS加解密
case 1.
使用wireshark抓取一个TLS的握手过程来简单示例。其中Client Key Exchange, Change Cipher Spec, Encrypted Handshake Message在一个数据包中返回。
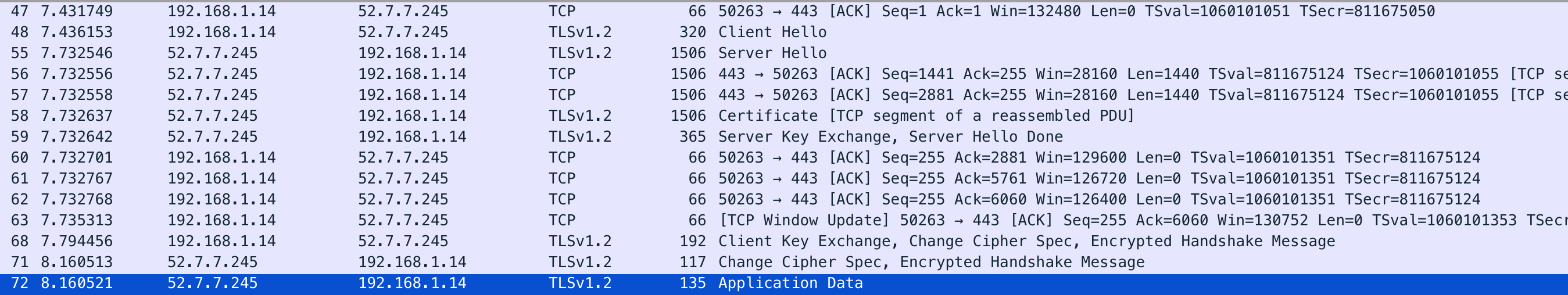
我在网上找到了严格一致的流程分析图(画的真不错)。
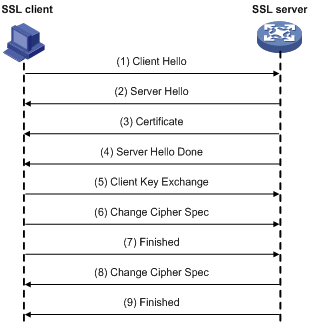
计算对称密钥的过程:
- 在
Client Hello阶段生成random_C - 在
Server Hello阶段生成random_S - 在
Client Key Exchange阶段,客户端根据这两个随机数,生成Pre-master,并用公钥加密,发送给服务端 Change Cipher Spec阶段,服务端私钥解密,获取PRe-master,用同样的算法计算加密密钥。
关于Change Cipher Spec Protocol
The change cipher spec protocol is used to change the encryption being used by the client and server. It is normally used as part of the handshake process to switch to symmetric key encryption. The CCS protocol is a single message that tells the peer that the sender wants to change to a new set of keys, which are then created from information exchanged by the handshake protocol.
实际上用于通知peer使用当前协商的密钥进行通讯
参考文章: